Executive Summary
The administrator password was easily guessable which allows any user to gain access to the administration dashboard. Having that access the attacker can leverage the fact that the blog is running a version that is out of date. Any attacker could utilize the vulnerabilities within the blog to gain access to the host running the blog and run commands on it. Moreover, the user within the server has access to run a specific file as the super admin user ( root ) which can allow the attacker to control the server with no limits.
Recon
first let's add the IP of the target to the host file and name it nibbles.htb
<target-ip> nibbles.htb
Before throwing any nmap scans at the target it is a good practice to just go to the browser and try to browse to it. this will allow us to discover if port 80 is open without making any scans.
Doing so shows that indeed port 80 is open and we are greeting with a simple hello world string
doing a curl on it shows us some interesting information
curl -L http://nibbles.htb # -L to follow any redirections
we found the following comment
<!-- /nibbleblog/ directory. Nothing interesting here! -->
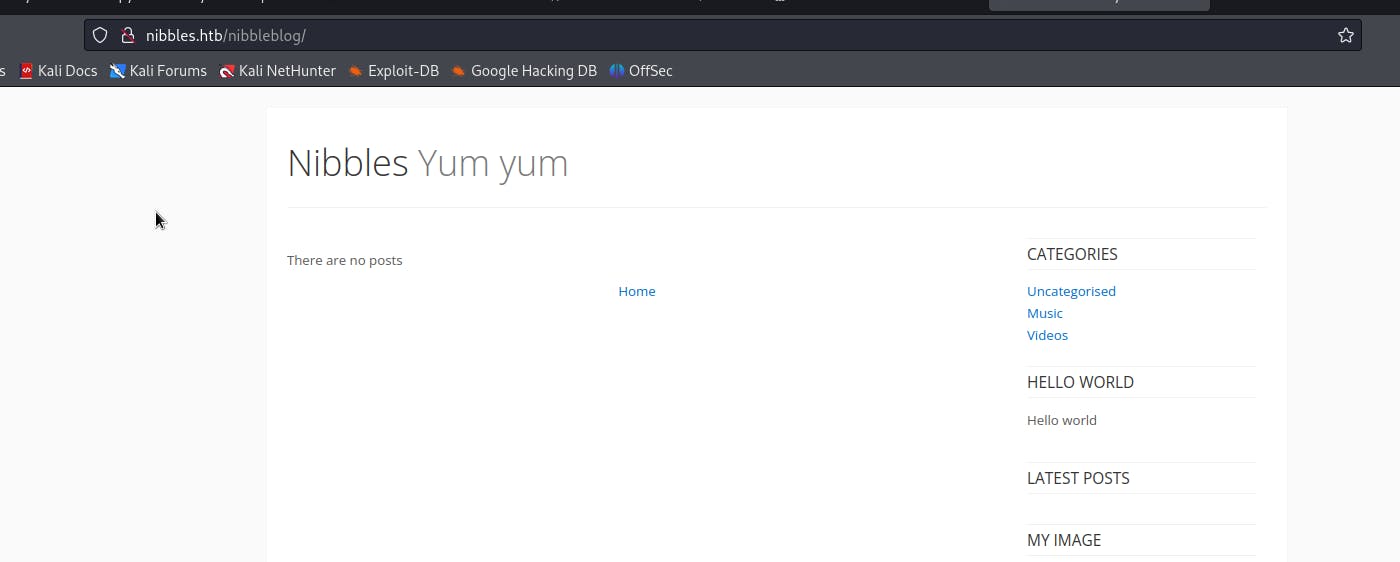
going to that page we find the homepage of the nibbleblog
Running scans
now that we found the page lets run some scans.
running Nmap to find other ports
scanning the site with gobuster to find interesting directories
gobuster
running gobuster like
gobuster dir -u http://nibbles.htb/nibbleblog/ -w /usr/share/wordlists/dirb/common.txt
this shows that there is an admin.php page

Also the /admin path leads to showing some interesting folders that should not be visible by anyone

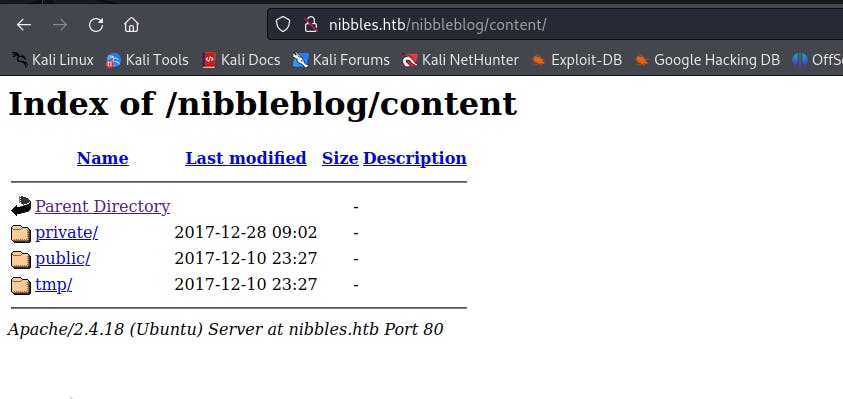
Also, there is another folder called /content which is interesting
Let's enumerate to find out if we can find any legit user names or passwords
bingo going to the /content/private we found the users.xml file which gives us a few important clues
there is a user called admin
there is a rate limit so if we try many times we will get locked out so we cannot throw hydra at it and brute force the login.
Attempting login
I tried to manually guess the password of the admin user and we found that it is nibbles
logging into the admin area we found that the version of nibblesblog running is 4.0.3
Vulnerabilities
searching for this version we can quickly find that there is a file upload vulnerability https://www.exploit-db.com/exploits/38489 with a metasploit module https://www.rapid7.com/db/modules/exploit/multi/http/nibbleblog_file_upload/
exploit description https://packetstormsecurity.com/files/133425/NibbleBlog-4.0.3-Shell-Upload.html
Nmap Result
The Nmap scan took a while but found only 2 ports open 80 and 22 finding the service version with the default scripts we find that the target is running
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Apache 2.4.18 doing a searchsploit on version 2.4 we find a buffer overflow exploit on version 2.4.x
multiple/webapps/51193.py
https://www.exploit-db.com/exploits/51193 Note: this exploit requires a path to a .lua file which we don't have at the moment
OpenSSH 7.2p2 doing a searchsploit on openssh with this version we find a vulnerability that allows us to enumerate usernames https://www.exploit-db.com/exploits/40136 we can also use metasploit module for this https://www.rapid7.com/db/modules/auxiliary/scanner/ssh/ssh_enumusers/
Exploitation
File Upload Vulnerability
Following the description in https://packetstormsecurity.com/files/133425/NibbleBlog-4.0.3-Shell-Upload.html
When uploading image files via the "My image" plugin - which isdelivered with NibbleBlog by default - , NibbleBlog 4.0.3 keeps theoriginal extension of uploaded files. This extension or the actual filetype are not checked, thus it is possible to upload PHP files and gaincode execution.
we can utilize the php reverse shell file located in /usr/share/web-shells and updating our IP Note: the above reverse shell did not work ( the shell keeps hanging )so we utilized a simple shell with cmd and then url encoded the reverse temp shell and passed it to get a revshell address to get a shell then we can start a netcat listener in our machine
nc -lvnp 1234
once we visit the image.php we will get a shell now we visit
http://nibbles.htb/nibbleblog/content/private/plugins/my_image/image.php
now we need to stabilize our shell we run
which python
and we could not find Python on the server we run
which python3
and bingo, it is there so we run
python3 -c 'import pty;pty.spawn("/bin/bash")'
and we get a better shell however we still have to do more. we click ctrl+Z to background it and then
stty raw -echo; fg
then we hit enter twice and now we have a stable shell.
Local enumaration
now that we are on the server we need to enumerate to find more information
running
whoami
we found that we are running as the nibbler user
we go to the home folder of nibbler user and we find the user.txt which contains the user flag. we can also find a zip file called personal.zip so we unzip it.
Now Running
sudo -l
we find out that we can run /home/nibbler/personal/stuff/monitor.sh as root with NO Password

Now all we have to do is add the line
/bin/bash
to monitor.sh and run it with sudo. it will not ask for a password and we will drop in a shell with root access.
